CrowdStrike is a cloud-based next-generation antivirus, EDR (endpoint detection and response) solution. You can deploy CrowdStrike in your infrastructure via a single lightweight agent. In this post, we will discuss how we can install CrowdStrike falcon agent / Sensor using Intune on Azure Ad joined devices.
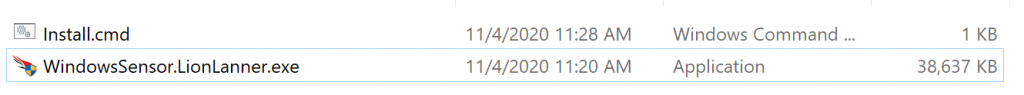
- Use the following code in Install.cmd. You should use your own CID (Customer ID)
@ECHO OFF
SET ThisScriptsDirectory=%~dp0
WindowsSensor.LionLanner.exe /install /quiet /norestart CID=02A1C79U38044E2XXXXXXX-FA
CrowdStrike Falcon Agent Install Switches
| CID= | Customer ID Checksum, which is required when installing. |
| MAINTENANCE_TOKEN= | Bulk Maintenance Token is retrieved from the CrowdStrike site when performing upgrades. |
| /install | Install the sensor (default). |
| /passive | The installer shows a minimal UI with no prompts. |
| /quiet | The installer shows no UI and no prompts. |
| /norestart | Prevents the host from restarting at the end of the sensor installation. |
- Now create an Intune package using Intune Packaging App. (Change source path and destination folder path)
PS C:\IntuneAppsWinAppsUtil> .\IntuneWinAppUtil.exe
Please specify the source folder: C:\CrowdStrike
Please specify the setup file: Install.cmd
Please specify the output folder: C:\CrowdStrike
Do you want to specify catalog folder (Y/N)?N

- Select App Package file which we created earlier.

- Add app information such as Name & Publisher

- Specify the commands to install and uninstall this app

- Select both OS system architecture and minimum OS to Windows 10 1607

- On detection rule, select “Manually configure detection rules and Rule type Register”

Path : C:\Program Files\CrowdStrike
File or folder : CSFalconController.exe
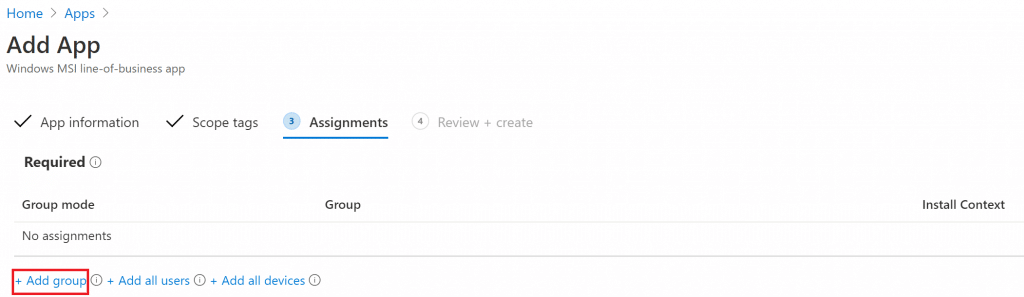
- Assign to the group you want to deploy printer using Intune.